News
How Cyber Insurance Is Evolving Amid Ransomware Tsunami
With the recent upsurge in ransomware attacks have come a few huge payouts from insurance companies, so they are cracking down on rules and regulations to lessen their exposure.
"Remember, a lot of what we talked about in cyber security and cyber insurance right now is 100 percent different from what it was just five or six years ago," said IT expert John O'Neill Sr. during yesterday's half-day online summit presented by Virtualization & Cloud Review, titled "Modern Hybrid Cloud Data Backup & Recovery," now available for on-demand viewing.
O'Neill Sr., chief technologist at AWS Solutions, was presenting with partner Dave Kawula, managing principal consultant at TriCon Elite Consulting.
Hardware Rotation
One way cyber insurers have evolved was detailed the duo's response to an audience member's question about whether the standard five-year hardware rotation scheme is still logical for smaller businesses.
 "A lot of cyber insurance policies have riders now that if you run out-of-support hardware, you could be in violation of your policy."
"A lot of cyber insurance policies have riders now that if you run out-of-support hardware, you could be in violation of your policy."
Dave Kawula, managing principal consultant, TriCon Elite Consulting
"I think that one of the big pieces -- and you know, John, I'd like you to maybe speak on this -- is the fact that a lot of cyber insurance policies have riders now that if you run out-of-support hardware, you could be in violation of your policy," Kawula noted. "So if your hardware gives you a 60-month, five-year warranty, and that's it, that could be your locked-in rotation for that."
O'Neill Sr., the cyber insurance expert among the two, replied: "Dave, you know, I spend a lot of time working on cyber insurance, particularly to understand its evolution and what it's doing. Because ultimately, I want folks to have insurance that will pay out when they need it to pay out, not just a policy that gives them this warm and fuzzy [feeling] that 'Okay, I have insurance, it's going to be there.' Because as you mentioned, there are many new fine-print items, if you will -- riders -- underwriting requirements, these kinds of things, that when you have an event, and they do a forensic analysis, if any of these things you attested to, you said, 'Yeah, I don't have any unsupported equipment,' and you do, they will use that to not pay. And you can argue, you can stomp your feet, but you're still out all that money and everything. So that's horrible.
 [Click on image for larger view.] The High-Level Checklist
[Click on image for larger view.] The High-Level Checklist
"And they are getting stiffer and stiffer on the requirement that your software and hardware, the manufacturer supports it. So all those companies that call you and say, 'Hey, you know, we know that Dell stopped supporting this model, but we'll take care of supporting it for you and everything else, and that'll be good by your insurance company.' That isn't true. I've analyzed numerous cases of that. And the reason that the insurance carriers don't accept that is because they have proven that no one but the manufacturer can readily address a security fix. And no matter what subsystem it appears, so whether it be in the base firmware, whether it be in, you know, the UEFI, or whether it be in your NIC firmware, whatever it may be only the manufacturers who they trust to fix that. And so that's why this is an issue.
So my suggestion is that you verify what the lifecycle of this -- this hardware that you're going to purchase -- directly with the vendor, extend your warranty coverage out as long as you can, and consider alternate options. Because a lot of people --particularly right now, right -- people are starting to get a little nervous with some of the investments to make right now and that sort of thing with the economy. So consider other options, such as cloud-based backups, solutions, or those type of things."
How Often Do Victims Pay Out?
O'Neill Sr. also answered an audience question about how often organizations have to ultimately pay a ransom demand.
"So actually, in preparation for an upcoming discussion, I have been just in the last couple of weeks reviewing data from numerous insurance carriers on this exact question," O'Neill Sr. replied. "And what it's looking like right now, is about a 50/50 split. So what that means is that out of the claims made they were analyzing about 50 percent of those claims involve paying some level of ransom or fee to the attacker.
"Now, of the other 50 percent, don't just assume that those are because those people had a better DR strategy. And they were able to thwart the attacker and recover everything without paying the ransom. There's a number in there that represent people that couldn't pay the ransom. And by couldn't, I mean, that not just that they didn't have that slush fund, or they didn't have the money available, but that the attacker was on a terrorist watch list or something like that, where the government prevents them being paid."
A recent ransomware trends report also provided data about payouts, finding that many victimized organizations paid ransoms and recovered their data, but nearly as many either recovered their data without paying the ransom or paid the ransom and still didn't recover their data.
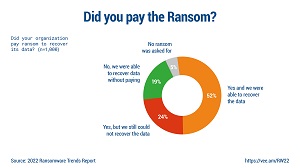 [Click on image for larger view.] Did You Pay the Ransom? (source: Veeam).
[Click on image for larger view.] Did You Pay the Ransom? (source: Veeam).
The report also detailed how ransoms were paid.
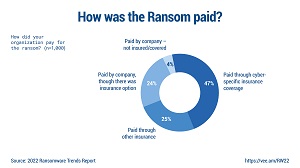 [Click on image for larger view.] How Was Ransom Paid? (source: Veeam).
[Click on image for larger view.] How Was Ransom Paid? (source: Veeam).
Yet another recent report revealed the top motivations to pay.
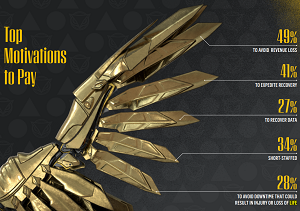 [Click on image for larger view.] Top Motivations to Pay (source: Cybereason).
[Click on image for larger view.] Top Motivations to Pay (source: Cybereason).
Reimbursements, Not Direct Payments
The subject of how insurance carriers pay out ransomware claims -- if you've dotted all your I's and crossed all your T's so they are absolutely forced to -- also came up.
"The cyber insurance vendor actually doesn't prepay those funds," Kawula noted. "They don't just have a slush fund sitting there and say, 'Hey, listen, yeah, we're gonna pay the 30 grand.' No, this customer has to come up with that. And it's a reimbursement mechanism. So in regards to that scenario where you might have to pay, John, is there a potential scenario where, let's say that you were caught, and you did have to pay -- which a lot of customers have, it's big business ransomware -- how do you pay that? Is that something that cyber insurance does, takes care of for you, or you have to have a fund set aside to actually take care of that?"
The reply: "Well, you absolutely have to have some sort of mechanism, whether it be a line of credit, or something, that you can pay it. And to explain that, I'll give a little bit of background. So your insurance policy, there's a few different areas to it, and the ones that you are most concerned with are that pay for loss. So you having to pay the ransom, or you having to replace hardware, you having to pay consultants, all those kinds of costs. And then there's the part that pays for loss of business, right? If you're a large organization, and you're down, and let's say your revenue generation is, you know, $100,000 a day or $1 million a day, whatever that is, you're losing that, because you're down -- had to stop -- and you can't afford to pay your employees, you can't afford to pay your vendors, you know, that has a great impact. So your insurance policy typically has a loss-of-business clause.
"Now, conventionally, these things are pretty easy. So you have a fire, they know where the fire started, they know what the cause of it was, they can estimate the recovery pretty quickly and accurately and start getting payments out. With cyber, it's gotten a lot more complicated. It used to not be as complicated and everybody kind of got a false sense of security. But the only reason it wasn't complicated is because the insurance companies didn't really understand it, like they do now.
 "So now they understand more. And so they're going to do a lot of forensic analysis before they pay out on anything."
"So now they understand more. And so they're going to do a lot of forensic analysis before they pay out on anything."
John O'Neill Sr., chief technologist, AWS Solutions
"So now they understand more. And so they're going to do a lot of forensic analysis before they pay out on anything. So you know, if you have a total of $4 million loss, you have to absorb that for at least some period of time. Even if you met all your covenants and everything is good, and the insurance company is gonna give you a check, there's still a period of time that's gonna pass, and it's not going to be a matter of days, it's going to be a matter of weeks or longer. So be prepared for that, if it's a setback on your cash reserves, or if it's a line of credit, or whatever it is, but make sure your organization is prepared to pay for some level of cyber incident remediation."
Validating Disaster Recovery
Yet more cyber insurance evolution was discussed in the context of needing to validate disaster recovery (DR) mechanisms.
"Cyber insurance vendors are making it much more difficult to gain access to the policies, and they're becoming way more stringent on what's going on," Kawula said. "So your ability to recover, and being able to prove that you can recover, and showing that you actually have a plan in place for a cyber attack, is actually very beneficial for most organizations, because the cyber insurance vendors will look at that, like, 'Listen, we're not just going to be caught in a situation where we're unprepared -- we are fully prepared for when this happens, and this is the steps and the processes that will take,' you could actually potentially receive a discount on your premiums that you're paying, because you're ahead of the game. Would you say that's a fair statement, John?"
 [Click on image for larger view.] DR Validation
[Click on image for larger view.] DR Validation
"Yeah, absolutely," O'Neill Sr. replied. "You know, the, the thing that I tell people to consider -- and they've never really done this -- is that if you go to your insurance broker, your carrier, during the renewal process, right, you engage them early, and you show them the steps you've been taking -- the processes and procedures you've changed and how you've tested your backups in any investment you've made and spare hardware or replacing out of date hardware, getting rid of those outdated operating systems, take them all of that and not only will that help you obtain the insurance that you want, it will help keep your prices down. And often, in some cases, it can lower the cost of your premiums more than it costs you to do it.
"So, for instance, we had a scenario where a service that we were engaging in for threat expert validation was costing around $90,000 a year. In this instance, we took that and we presented it to the insurance carrier, and they came back and they gave us a $130,000 reduction on premiums. So if you think about that, that means we were actually kind of paid $40,000 to increase our security infrastructure. But if you don't bring it to them, if you don't discuss it with them, if you don't present it to them, if you don't validate it with them, they'll never take that into account, and you'll lose out on that possible benefit."
Insurers Take Over
O'Neill Sr. also dispelled the idea that ransomware victims are in charge of the response after an attack, with cyber insurance companies only getting involved when it's time to write a reimbursement check. That's not the case, as they want to take control of forensics and other after-attack work themselves, including negotiations with the bad actors.
As part of that, insurers may have a predefined list of what are sometimes called panel providers, basically authorized vendors in specific areas. They might be law firms or auditors who send in response team specialists to coach victims about the response.
"And these are companies where they are bringing them in for the forensics, the loss mitigation, the response, all that kind of thing," O'Neill Sr. explained. "And the reason that I bring this up, because I want to give a tip to everyone, is that you're not limited to these. If, before something happens, you go to your insurance company, and you say, 'Hey, we have this great security partner XYZ organization. And we'd like to get them added to the response provider list that's authorized, so that if we ever have an issue, we can engage them.'
"And many times, your insurance company will have no problem with that. And they'll work with that vendor to authorize them and get them on that list. And that way, when you have that event, you can call on that trusted partner you're already working with and use them. But if you don't do it in advance, when the event happens, if you try to say, 'Hey, I want to use that XYZ organization,' your insurance company is going to say, 'No, if we're going to pay out, you're going to use our authorized folks.'"
Along with their detailed discussions of cyber insurance, the duo examined many other areas of hybrid cloud data backup and recovery. Topics include red team/blue team/cloud team security exercises, protecting container/Kubernetes implementations, protecting out-of-band networks and many more.
While their presentation is available for on-demand viewing, attending such events live brings the benefit of being able to ask questions of expert presenters (not to mention the chance to win a great prize). With that in mind, here's the schedule of upcoming summits: