News
'Stop Doing That!' Multi/Hybrid Cloud Cybersecurity Advice for RDP, Credentials and More
Veteran cybersecurity experts working on the front lines are left shaking their heads when they have to deal with organizations whose security postures are still wide open to well-known, longtime vulnerabilities.
Here's an example.
"And I still am baffled by this, that brute-force RDP attacks are still one of the most common attack vectors that are out there. Okay, everyone walking away from this session, if you have open-ended RDP connections on the internet, number one: Stop doing that!"
The speaker is Dave Kawula, managing principal consultant at TriCon Elite Consulting.
The subject is Remote Desktop Protocol (RDP), a proprietary protocol developed by Microsoft which provides a user with a GUI to connect to another computer over a network connection, according to Wikipedia.
The venue is a recent half-day online summit presentation hosted by Virtualization & Cloud Review, titled "Multi-/Hybrid Cloud Security & Recovery," now available for replay.
The gist is something like, "Why in the heck are people still leaving themselves exposed to vulnerabilities everybody has known about forever?"
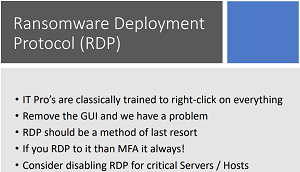
RDP tops that list, being such a popular target for threat actors that it has been dubbed the Ransomware Deployment Protocol. "Remote Desktop Protocol (RDP) is the most popular initial ransomware attack vector and has been for years," said Palo Alto Networks in a post that itself is now more than a year old.
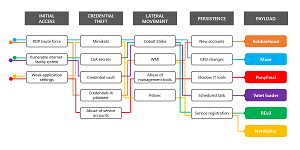 [Click on image for larger view.] Brute Force RDP Is Prominent Initial Access Vector (source: Microsoft).
[Click on image for larger view.] Brute Force RDP Is Prominent Initial Access Vector (source: Microsoft).
"It is extremely easy to expose RDP unintentionally by leaving RDP exposed on a forgotten system, cloud instance, device previously protected by network segmentation or by directly connecting to the internet," Palo Alto said. "What's worse is that RDP has become more widespread, more exposed and a more prevalent risk that can lead to attacks -- specifically ransomware deployment -- loss of data, expensive downtime and remediation efforts, as well as brand damage for organizations."
It's that "directly connecting to the internet" aspect that still baffles Kawula and prompted him to make his "number one: Stop doing that!" comment.
He followed up.
"Number two, if you need to do that, lock it down to a specific set of IPs that you trust so that it's not open ended on the internet, in the same way that when you set up a Microsoft Azure VM, all of those RDP ports are shut down on that external interface.
 [Click on image for larger view.]
[Click on image for larger view.]
"And you can do that by default with a few simple configurations. And now in the network security gateway, you can go in there and you can say, 'Oh, I want to open this up only from my current IP address that I'm at right now.' So if you're having to connect in from the hotel or something like that, you can easily do that, but don't leave open-ended RDP on out there.
"Number three, is that we like to call RDP now the 'ransomware deployment protocol,' because if you have weak passwords, those brute-force attacks are going to find them real fast. So if you are opening up RDP, and you're using RDP, for goodness sakes, make sure that you've got account lockout thresholds put in there on your security policies. I always recommend that people run the latest security benchmarks. Like, for example, from Center for Internet Security, at least Level 1 to lock some of the stuff down. But, yeah, this is still a huge attack vector out there.
 "And for heaven's sakes, if you are going to enable RDP on anything, even desktops, make sure that you're turning on Multi-Factor Authentication, because you just don't RDP without MFA anymore."
"And for heaven's sakes, if you are going to enable RDP on anything, even desktops, make sure that you're turning on Multi-Factor Authentication, because you just don't RDP without MFA anymore."
Dave Kawula, managing principal consultant, TriCon Elite Consulting
"And for heaven's sakes, if you are going to enable RDP on anything, even desktops, make sure that you're turning on Multi-Factor Authentication, because you just don't RDP without MFA anymore."
With that, Kawula turned to his presentation partner, John O'Neill Sr., chief technologist at AWS Solutions, for his follow-up take on the matter.
"I'm just gonna be really quick here, and mention one thing that I still see a lot," O'Neill Sr. replied. "And it's a huge threat vector. And that is, that is RDP left open on servers, for reasons that you really shouldn't be using RDP. For example, I run into organizations where I'm brought in because something happened, and I go look back at it. And there were RDPing into domain controllers to do basic tasks, like add a user into Active Directory, and things like that. And I can tell you as much as RDP is abused, I try to avoid using RDP on those kind of systems as much as possible.
 "And then the other thing, Dave, that that you and I see, and it's -- it's kind of astonishing, in some ways -- is that when RDP is enabled, nothing is done to restrict down other communication vectors or endpoints."
"And then the other thing, Dave, that that you and I see, and it's -- it's kind of astonishing, in some ways -- is that when RDP is enabled, nothing is done to restrict down other communication vectors or endpoints."
John O'Neill Sr., chief technologist, AWS Solutions
"And then the other thing, Dave, that that you and I see, and it's -- it's kind of astonishing, in some ways -- is that when RDP is enabled, nothing is done to restrict down other communication vectors or endpoints. You mentioned giving specific endpoints and that kind of thing. But I will see where the switch, there is no traffic regulation to that device. So let's say you have a dedicated DHCP server or something like that. And it's answering requests on port 25 and port 110 and all these ports that don't need to be enabled. So, you know, take some time and tailor in your network protection to make it as hard as possible for someone to abuse the tools that you need to be able to be effective for your organization. But not leave you kind of stay in there. Make it in a crowd kind of thing."
Credentials
Some tools that might fall into the abuse trap are credentials, another source of bafflement to the veteran IT cybersecurity duo.
"Compromised credential are still a big issues for organizations," Kawula said during another part of the pair's two hour-presentation. "We're still getting called in to do wide-scale MFA projects, John, where the initial point of attack is just so easy to take and the bad guys to come in with. We see so many organizations that are out there right now, today, still using elevated generic service accounts.
"I'm telling you right now, if you want the absolute easiest way for bad guys to get into your network, just leave some elevated service accounts hanging around."
"I'm telling you right now, if you want the absolute easiest way for bad guys to get into your network, just leave some elevated service accounts hanging around. And I'm going to tell a little story with this John. And the story goes a little like that. We want to use in our organization Some type of desktop management solution, the desktop management solution happens to have the ability to install patches and software and gain inventory on machines. Well, we didn't read the fine print that said that we need to take and have customizations and those rights that are required on those devices. So we leave that service account hanging around on all of these devices. In comes COVID-19, a couple of years ago, and we immediately send everybody home. All of these laptops, or all of these devices that were working on our corporate network, are now taking and are now sitting on a home network connected over an everything-access VPN, nothing locked down, because we were all pushed in it to do things so fast and get the businesses back up and running."
 [Click on image for larger view.]
[Click on image for larger view.]
When something happens on that home machine that indicates to threat actors it's now on an insecure network, the trouble starts, Kawula said.
"And they gain access to that service account. Well, la dee da, John, that service account happens to be a member of the domain admins group. So boom, you're done, right there. And so, if you don't think this is happening, go and do a review of all of your service accounts inside of Active Directory and go double-check what rights they have. If they have, for example, log on locally, right? Can someone please explain why a service account needs the ability to log on locally? I don't know. And it's also a developer-level issue as well to where, John, we run into the problem all the time where we're installing software and we're told, 'No, that needs admin rights -- I really challenge that.' And so when we take and we look at compromised credentials, still a big issue today, a lot of organizations haven't fully migrated over to group managed service accounts or other things that can help protect them. So I don't know, I'll stand off my soapbox. Now, John, and I'll hand this over to you. Because I know you've got a lot to add here."
Indeed, the insistence on unneeded admin rights is a sore spot with O'Neill Sr., too.
"Well, I'm about to probably lose a few friends out there, but I'm just gonna go straight at it. And I'm going to focus on the thing that I'm dealing with the most right now, which is IT pros that just continually insist that they have to have admin rights to everything, right? And it starts with, 'Well, I need to be a domain admin.' Well, really, you don't really do anything with domain controllers. So why do you need to be a domain admin? And there's numerous reasons. So then you get them off that and it's, you know, 'I need to be this level of admin or that level.' And even when they're on local PCs, and they're like, 'Well, I need to be an admin, because I have to change an IP address, you have to do this.' No, you don't. That's the easy way to do it. Okay, but the principle of least privilege -- which is not new, but is certainly something that we all need to be following to fend off the threats row -- and the principle of least privilege says, you use the minimum amounts required to accomplish a task. And nothing more. Well, if you're running as an admin to do something simple, like change IP addresses, that's more than you need to accomplish that.
"Now, I get it, that we're always balancing between workload and that sort of thing. So if you're only changing an IP address on a machine, once a year, so be it, right, you're gonna do it as an admin. But let's say that this is something where you're using it to connect to a dedicated piece of equipment and you're changing it once a day, or once a week, you really should take the time to identify the specific credentials that you need the right you need, add those to an account and nothing more, do it that right way.
"Unfortunately, a lot of our fellow IT pros take offense when I say that, 'Well, you know, I'm an IT pro, I'm an expert, I should have admin rights.' And what I tell them is that one, as professionals, we have an obligation to do the best we can to protect our organizations and our fellow employees at all times -- to take that out of the mix.
"If my organization is attacked, and it comes through a credential that I have an elevated credential or something like that, it's not going to make my employers feel any better that I say, 'Well, I needed it for this or I need it for that.' All they're going to see is that their their business was shut down. Their operations were impacted, those expenses were there."
"If my organization is attacked, and it comes through a credential that I have an elevated credential or something like that, it's not going to make my employers feel any better that I say, 'Well, I needed it for this or I need it for that.' All they're going to see is that their their business was shut down. Their operations were impacted, those expenses were there.
"And the third reason is, is when that happens, when you are part of the IT team and an organization that is compromised, you will never ever be able to scrub that from your resume -- it will live with you for the rest of your career. So, you know, as I mentioned, I don't make a lot of friends. But my job here isn't to make friends. It's to share what we see in the field and the best way that we think that our fellow IT pros can protect themselves and their organizations."
More Bewilderment
O'Neill Sr. and Kawula also expressed amazement about other unsafe practices they still commonly run into, which, just for a few examples, include:
- Not subscribing to advanced threat protection
- Running IT systems that still use passcodes for MFA
- Not following Payment Card Industry (PCI) standards, leading to things like exposed credit-card data
- Not implementing cell phone port protection
- Not using MFA
- Browsing the internet from servers (especially with Internet Explorer)
The two-hour presentation from O'Neill Sr. and Kawula was also filled with many other eye-rolling, head-slapping, face-planting moments.
As noted, they can be revisited with an on-demand replay of the half-day presentation, but there are advantages to attending such online events live, such as being able to ask questions of the experts (and maybe win a cool prize raffle). With that in mind, here are some events coming up over the next month or so: